Infrastructure Cybersecurity: Pipelines
KEY TAKEAWAYS
- The ransomware attack on the Colonial Pipeline highlights the vulnerabilities of pipeline systems to cyberattacks and the effects of a slowdown or halt in key locations.
- The federal government has primary responsibility for protecting the nation against cyberattacks. Private industry and the federal government share responsibility for securing pipeline infrastructure.
- Lawmakers have expressed bipartisan, bicameral support for legislation requiring operators of critical infrastructure to report cybersecurity incidents to the federal government.
The U.S. energy network includes nearly 3 million miles of pipeline transporting oil, natural gas, and other critical substances. Private industry and the federal government share responsibility for securing this important piece of infrastructure. The recent ransomware attack on the Colonial Pipeline has highlighted the vulnerabilities pipeline systems have to cyberattacks and the ripple effects that can result from a slowdown or halt in key oil pipelines.
Multiple Vulnerable Points in the Oil Processing Network
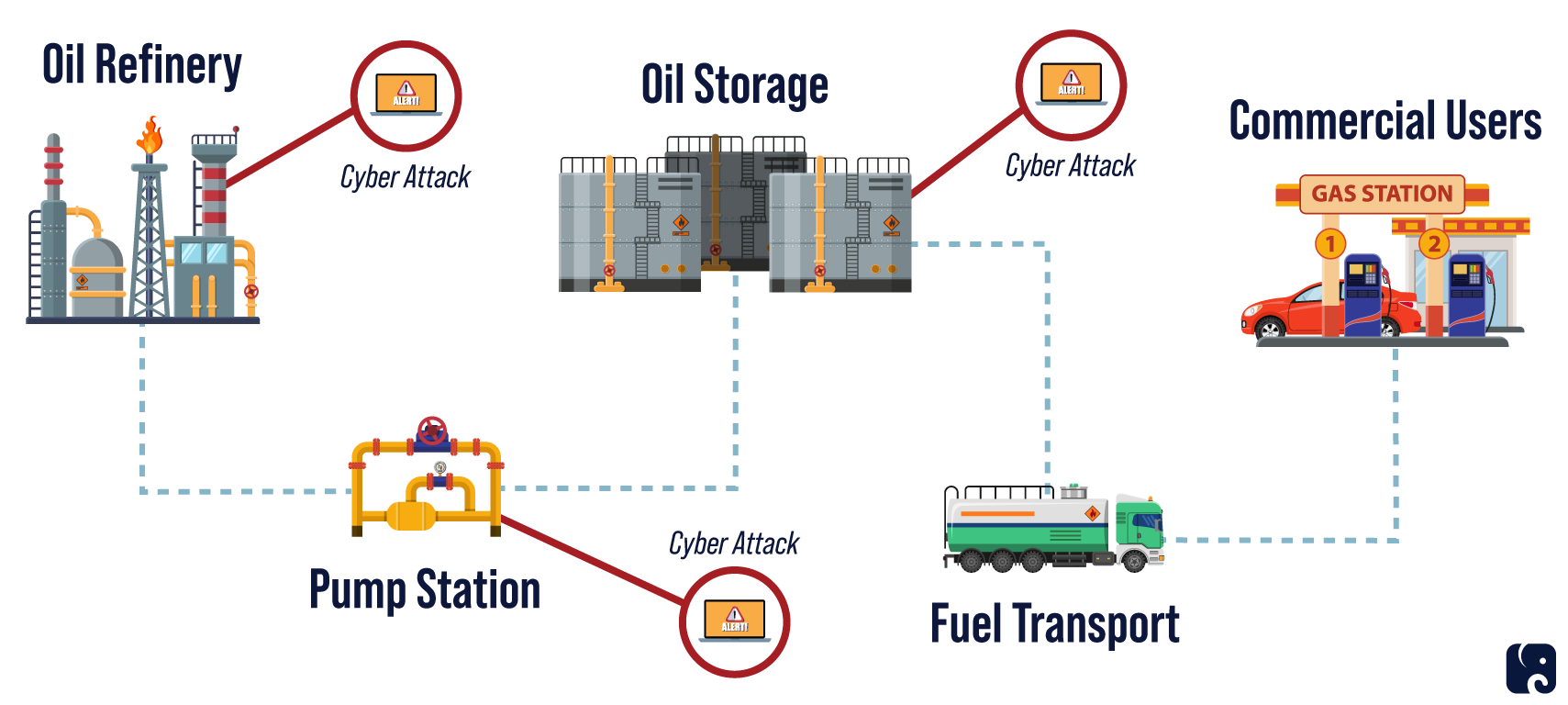
the colonial pipeline attack
On May 7, Colonial Pipeline Company learned it was the latest U.S. business to become the victim of a ransomware attack. The FBI identified the attackers as a ransomware-for-hire criminal enterprise based in Russia that calls itself “DarkSide.” The group took over parts of Colonial’s systems, and demanded the company pay a ransom to get back control.
The company shut down the pipeline, which runs from Texas to New York and delivers about 45% of the fuel used along the eastern seaboard. The pipeline was restarted on May 12, but the five-day stoppage caused fuel shortages up and down the east coast and increases in gas prices. One North Carolina school district even abandoned in-person classes for a day due to concerns staff and students might not have enough gas to get to class.
Ultimately, the company decided to pay a ransom of around $4.4 million in bitcoin to the hackers in order to regain control of its systems. The CEO said that he authorized the ransom because the company was unsure how badly the attackers had breached its system and consequently how long it would take to bring the pipeline back. He testified before the House Committee on Homeland Security that paying the ransom was the “toughest decision I have had to make in my life,” but in the end restoring critical infrastructure as quickly as possible was the “right thing to do for the country.” While the FBI advises against paying a ransom, under current law paying ransom to hackers is legal as long as the recipient is not an entity or individual sanctioned by the Treasury Department.
Ransomware criminals are aware of this dynamic, and many of them target entities and industries where down time has such a significant effect that victims will choose to pay the ransom because of the urgent need to get back online. These include hospitals, schools, municipal governments, advanced manufacturing, and critical infrastructure like pipelines. The Colonial Pipeline attack was reportedly facilitated by a very simple hack: a compromised password from an outdated account. If the company had multi-factor authentication in place, the hack likely would not have been successful.
On June 7, the Justice Department announced it had tracked and seized about $2.3 million of the ransom Colonial Pipeline paid to the DarkSide group. This is a significant achievement for DOJ, which worked with the company to identify and track the ransom payments through multiple transfers designed to throw law enforcement off the trail. Tracking ransom payments is one promising tool among the techniques the public and private sectors must deploy to fight ransomware.
federal government must up its game
The Transportation Security Administration is the chief federal agency responsible for pipeline security. The Department of Homeland Security works in consultation with the Department of Transportation in regulating the transportation of hazardous materials by pipeline.
The Colonial Pipeline attack illustrates the critical need for the Biden administration to address long-standing cybersecurity challenges. The Government Accountability Office has identified critical actions the federal government must pursue with urgency to ensure the cybersecurity of the nation, including “strengthen the federal role in protecting the cybersecurity of critical infrastructure” such as pipelines.
In 2018, GAO issued a report highlighting weaknesses in TSA’s management of its pipeline security efforts. The report included 10 recommendations. Three of those, pertaining to cybersecurity workforce development, risk management, and developing more accurate data sources, have yet to be fully addressed. The report also noted that TSA lacked “the required level of cybersecurity expertise necessary to carry out its pipeline security responsibilities.”
On May 27, TSA issued its first ever pipeline-focused security directive. The directive represents a shift from the agency’s collaborative approach to voluntary pipeline cybersecurity standards. Historically, TSA has relied on the pipeline industry adhering to voluntary pipeline security guidelines. The guidelines serve as the de facto standard for pipeline security programs and were developed in close coordination with the industry. Under the new TSA directive, pipeline operators will now be required to align with federal cybersecurity guidance. Specifically, the directive requires pipeline operators to report cybersecurity incidents to the Cybersecurity and Infrastructure Security Agency, establish a cybersecurity coordinator, review their current activities against TSA’s guidelines to assess cyber risks, identify gaps, and develop remediation measures.
President Joe Biden reportedly gave Russian President Vladimir Putin a list of 16 critical infrastructure entities that are “off-limits” to Russian cyberattacks. This is likely the same 16 critical infrastructure sectors designated by CISA “whose assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof.” Pipelines are a subsector of the transportation systems sector. Cybersecurity experts, Russia observers, and people with common sense are skeptical merely providing the list to Putin will have any impact on Russia’s continued use of cyberattacks on U.S. entities.
national cybersecurity incident notification
The fallout from the Colonial Pipeline attack, including reports that the company did not notify CISA that it had been breached, has reignited the “notification requirement” debate on both sides of the Capitol. The company did promptly notify the FBI.
CISA relies on voluntary contact and association with the private sector. In response to a question from Senator Rob Portman, the agency’s acting director testified before the Senate Homeland Security and Governmental Affairs Committee that he didn’t think Colonial would have reached out to CISA at all without the assistance and intervention of the FBI.
At another hearing, Senator Josh Hawley asked Jen Easterly, President Biden’s nominee to head CISA, whether the current framework of entities sharing information with CISA voluntarily was sufficient, or if Congress needs to require companies that operate critical infrastructure to notify the federal government when they have suffered a significant cybersecurity incident. Ms. Easterly replied: “It seems to me that voluntary standards are, probably, not getting the job done and that there, probably, is some sort of role for making some of these standards mandatory to include notification.” She also testified: “I do think it’s important that, if there’s a significant cyber incident, that critical infrastructure companies have to notify the federal government, in particular CISA. We have to be able to warn other potential victims.”
The chair and vice chair of the Senate Select Committee on Intelligence, Senators Mark Warner and Marco Rubio, are drafting legislation that would require federal agencies, federal contractors, and critical infrastructure owners and operators to notify CISA within 24 hours of suffering a significant cybersecurity incident. House Homeland Security Committee leaders also have expressed bipartisan support for advancing a cybersecurity incident reporting law.
General Paul Nakasone, the director of the National Security Agency and commander of U.S. Cyber Command, Director of National Intelligence Avril Haines, and FBI Director Chris Wray recently called on Congress to pass a national notification law. Some businesses also support a federal notification law, including Microsoft and FireEye. Many companies also advocate for reciprocity from the federal government in sharing information with the private sector when its systems or networks are compromised.
Next Article Previous Article
