The Threat of Ransomware
KEY TAKEAWAYS
- Ransomware is a type of malicious software that prevents users from accessing computer files, data, or networks until a ransom is paid.
- Hospitals, school districts, police departments, and city and state governments of all sizes have been targeted by cybercriminals using ransomware.
- There are a variety of things organizations can do to reduce the likelihood of a devastating ransomware attack, including backing up critical information and servers, testing their systems, and promptly patching known vulnerabilities.
Ransomware, a type of malicious software that prevents users from accessing computer files, data, or networks until a ransom is paid, has become an economic and national security threat. Hospitals, school districts, colleges, police departments, and city and state governments of all sizes have been targeted by cybercriminals using ransomware.
2017 WannaCry Ransomware Hit Worldwide
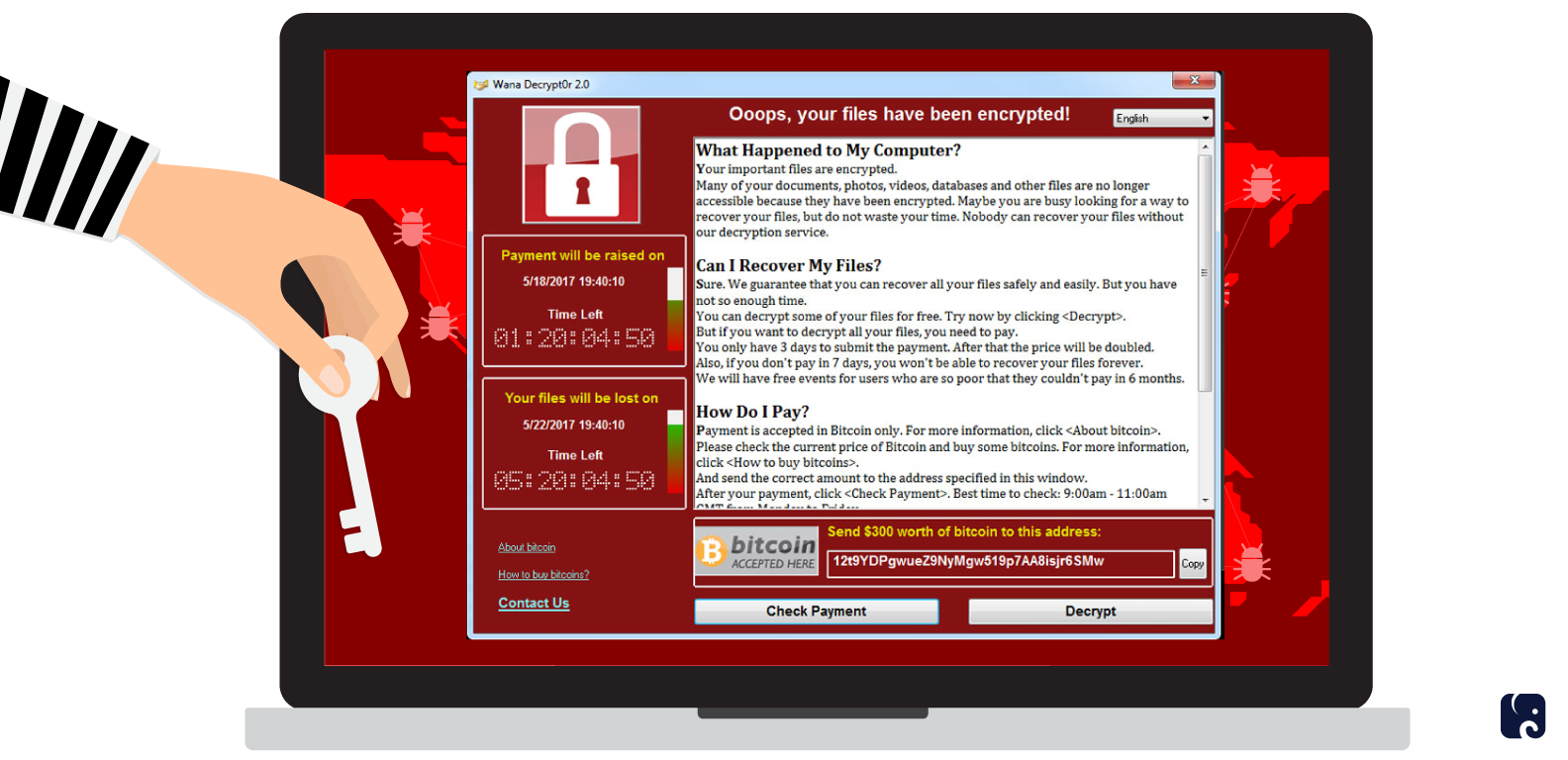
The 2017 WannaCry ransomware attack, named after the variant of software deployed, was a watershed moment in ransomware history. The virus infected hundreds of thousands of computers on at least 150 countries, shutting down global shipping giant FedEx and crippling the National Health Service in the U.K. The global economic damage was as much as $4 billion.
how it works
The recent experience of the Athens Independent School District in Texas provides a case study for ransomware attacks. A few days before the start of the school year, the district’s technology chief received a message saying that the school system’s computer network had been locked. The IT chief began exchanging messages with the hacker, inquiring how payment would be made and how much it would cost to unlock the system. As in most ransomware cases, the payment was to be made in bitcoin, a cryptocurrency that is difficult to trace and tie to a specific person. Criminals may even provide step-by-step instructions for victims to acquire bitcoin or another cryptocurrency.
In Athens, the hacker warned the IT chief not to contact the FBI or other law enforcement. The FBI generally advises victims not to pay the ransom, because there is no guarantee it will result in the restoration of data, victims may be targeted again once they have shown a willingness to pay, and paying the ransom encourages future attacks against others.
Organizations are not helpless in the face of ransomware attacks. There are a variety of best practices they can use to reduce the likelihood of suffering a devastating ransomware attack, including backing up critical information and servers; conducting a cybersecurity risk analysis of their organization; testing their systems; promptly patching known vulnerabilities; and having an incident response plan in place.
Traditional Ransomware Attack

While there is no centralized list of ransomware attacks, and not all attacks are reported, ransomware cases appear to have increased in number and in economic cost over the last few years. A survey of 5,000 IT professionals across the world found 51% of organizations were hit by ransomware attacks in 2019. The global average cost to remediate a ransomware attack was $761,106. In February, one FBI agent speaking at a trade conference said that from 2013 to 2019, victims paid about $144 million in ransom. Another report said ransomware was a $1.4 billion industry in the United States alone in 2019.
The threat of ransomware has only risen in the last year. A survey conducted last month by one cybersecurity firm found 56% of the organizations surveyed had suffered a ransomware attack in 2020. A report released in September found there had been a “seven-fold year-on-year increase in ransomware reports” and called it “the go-to mechanism for threat actors in terms of generating profit.” Another cybersecurity firm has referred to ransomware as an “epidemic” and predicted that a business will fall victim to a ransomware attack every 11 seconds by 2021. Ransomware damages are projected to have a global cost of $20 billion next year, 57 times more than in 2015, which would make ransomware the fastest growing cybercrime.
In October, the Treasury Department’s Office of Foreign Assets Control warned organizations making ransomware payments that they risk violating economic sanctions imposed by the U.S. government against cybercriminal groups or state-sponsored hackers. This could discourage victims from paying ransoms, which has the potential to undermine the entire ransomware business model for criminals.
But getting systems back online and restoring hacked data can take weeks and potentially cost more than the ransom. Government organizations may face additional pressure to pay so they can continue to provide services. IBM found attackers are targeting schools and universities during the coronavirus pandemic, as many have switched to virtual learning and have little tolerance for downtime. As the Athens superintendent put it: “No one wants to do this. It feels awful. But it could be worse if we didn’t pay. School possibly could have been delayed many weeks. We felt we had to.”
The Athens school board approved paying $50,000 in ransom to get key systems back online. They are not alone. A recent survey of IT professionals around the world found 27% of victims paid the ransom, averaging $1.1 million each. Some organizations have begun to buy cybersecurity insurance against data breaches and ransomware attacks. According to a 2020 report, more than 40% of cyber insurance claims now involve ransomware, and there was a 65% increase in the severity of claims reported from 2019 to 2020.
The incident in Athens ended on a happy note – the school district discovered a copy of a backup server that held the same data it was prepared to pay $50,000 to regain access to. The district broke off communication with the hacker, wiped and restored hard drives, and paid no ransom. Most cases do not have such a happy ending. Usually either a ransom is paid or victims spend significant time and money rebuilding systems and data, often from scratch. If the victim is a public entity, taxpayers end up paying for the ransom or for the cyber insurance premiums.
a wide-ranging threat
Hospitals have faced a string of ransomware attacks this year. While some hackers pledged not to attack hospitals and other health care institutions at the beginning of the pandemic, attacks against the sector increased 71% in October. The attacks come as some hospitals were already stretched thin dealing with the coronavirus. On October 28, the Cybersecurity and Infrastructure Security Agency, the FBI, and the Department of Health and Human Services issued a joint cybersecurity advisory outlining “credible information of an increased and imminent cybercrime threat to U.S. hospitals and healthcare providers.” The agencies described the tactics used by cybercriminals and outlined steps hospitals could take to reduce the risk and the impact of an attack.
Municipalities of all sizes also are frequent targets of ransomware attacks. One report found two-thirds of known ransomware attacks in 2019 targeted state and local governments. Governments are an attractive target: they have a steady revenue stream; often have outdated systems and poor cybersecurity practices; and place a premium on protecting citizens’ data and restoring services quickly.
In March 2019, one county in Georgia paid hackers $400,000 to regain access to its files. The attack had hit several departments, including the sheriff’s office. Faced with the prospect of taking months to get the systems back online, the county paid up.
In August, the University of Utah announced it had paid cybercriminals $457,000 to delete sensitive student and teacher data they had stolen from school servers. Taxpayers in Utah got off easier than those in California, where officials for the University of California in San Francisco authorized a payment of $1.14 million to unlock key school systems and decrypt important data.
In many instances, victims choose not to pay, agreeing with law enforcement that it only encourages future attacks. The city of Baltimore declined to pay a ransom of $80,000 when a ransomware locked down nearly all city computers last year. Instead, the city chose to remediate the situation. It ultimately cost the city $18.2 million to recover, including new hardware and deferred revenue. The mayor explained why the city chose not to pay the ransom: “Well, first, we’ve been advised by both the Secret Service and the FBI not to pay the ransom. Second, that’s just not the way we operate. We won’t reward criminal behavior.” In late November, the Baltimore County school system was hacked in another ransomware attack.
Cybercriminals continue to evolve new ways of using ransomware. One emerging issue is the rise of “double extortion” attacks. In this scenario, criminals don’t just lock the hacked material, they threaten to release sensitive information – such as employment files, medical records, or student files – unless the ransom is paid. In September, hackers posted personal information about students and employees of Virginia’s Fairfax County Public Schools system online as part of a ransomware attack.
Next Article Previous Article
